Next-Gen Cybersecurity
Empowering your business with proactive, adaptive, and intelligent cybersecurity solutions for a safer digital world.
🌟 Why Next-Gen Cybersecurity?
✅ Real-time threat detection
✅ AI-driven anomaly detection
✅ Automated incident response
✅ Advanced endpoint protection
✅ Compliance-ready frameworks
✅ Scalable for startups to enterprises
🔐 Next-Gen Cybersecurity Solutions for Your Business
Empowering Resilience in a Digital World
As cyber threats become more sophisticated, traditional security is no longer enough. Our Next-Gen Cybersecurity Solutions combine AI, machine learning, threat intelligence, and zero-trust architecture to provide proactive, adaptive, and intelligent protection for businesses of all sizes.




🧠 How It Works: Layered Cyber Defense
Diagram: Multi-Layered Cybersecurity Architecture
Layer 1: AI-Powered Threat Detection
Detect anomalies in real time using behavioral analytics.
Layer 2: Endpoint Protection
Secure every connected device with next-gen antivirus, EDR & patch management.
Layer 3: Network Security
Firewall, IDS/IPS & secure VPN tunnels with zero-trust enforcement.
Layer 4: Cloud & Data Security
Protect cloud workloads and sensitive data across environments.
Layer 5: Automated SOC
Centralized AI-enabled SOC to respond and recover swiftly.
⚙️ Key Features
1️⃣ AI-Powered SOC (Security Operations Center)
Detects and responds to threats automatically with predictive analytics.
2️⃣ Behavioral Analytics
Learns normal activity patterns to instantly flag anomalies.
3️⃣ Threat Intelligence Feeds
Global threat data integration for zero-day threat protection.
4️⃣ Automated Response & Orchestration
Reduces dwell time by executing real-time mitigation workflows.
5️⃣ Regulatory Compliance
Complies with GDPR, ISO 27001, HIPAA, and more.
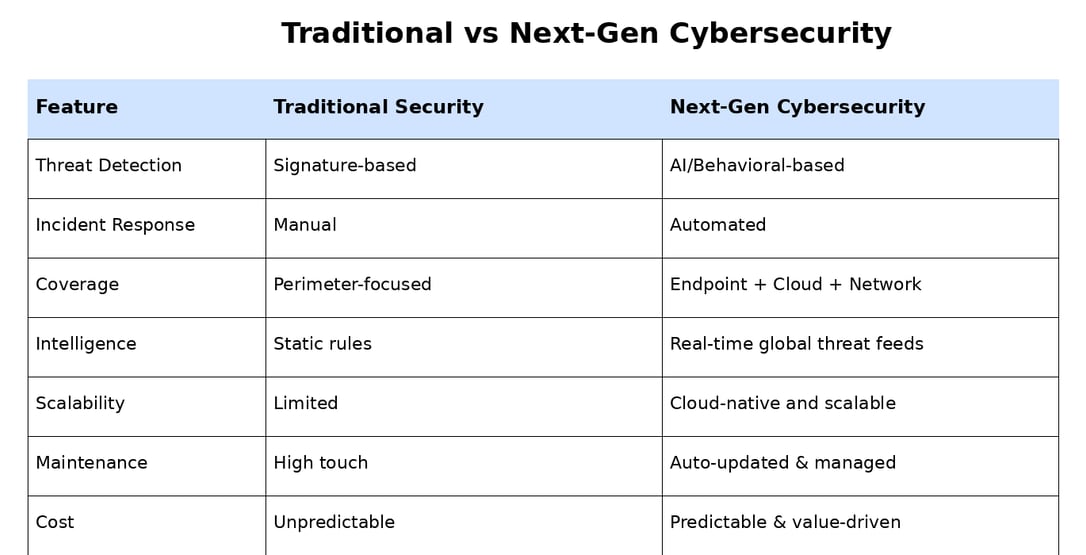
🛡️ Real-World Use Case: Retail Chain Secures Itself with AI-Driven SOC
🏬 Client Profile
A national retail chain operating 250+ stores across India, with both offline outlets and a growing e-commerce platform, was increasingly targeted by cyber threats. Their legacy cybersecurity system relied on a rule-based firewall and manual log reviews — insufficient for modern, AI-powered threats.
🚨 The Problem
Over 3 months, the company experienced:
Repeated ransomware attacks on POS systems
Multiple unauthorized login attempts from offshore IPs
Delayed incident detection, often taking hours to respond
Rising number of false positives overwhelming their IT team
Increased downtime at multiple outlets during peak sales hours
⚠️ Specific Incident
One night, an attacker gained access through a compromised employee VPN credential. Within 2 minutes, they started exfiltrating sensitive customer data and deploying ransomware to lock critical POS terminals.
Due to the manual nature of their security process, the alert went unnoticed until the next morning, resulting in:
₹42 lakhs in revenue loss due to 12 hours of downtime
Legal risk under data protection laws
Damaged brand reputation on social media
Loss of customer trust and loyalty
✅ Our Solution: Deployment of AI-Driven SOC
The retail chain onboarded our Next-Gen Cybersecurity Stack which included:
AI-Powered Security Operations Center (SOC) for 24/7 monitoring
Behavioral Analytics Engine to flag unusual login locations or user actions
Threat Intelligence Feeds updated in real time
Automated Incident Response (SOAR) for auto-containment
Zero Trust Network Access (ZTNA) for remote employees
Cloud Security Posture Management (CSPM) for their e-commerce infrastructure
🚀 The Outcome
📌 Time to Detect Threat: Reduced from 6+ hours to under 15 seconds
📌 Time to Respond: Automated mitigation began within 14 seconds
📌 Downtime Reduction: 0 business hours lost in subsequent attacks
📌 False Positives: Reduced by 72%, saving analyst time
📌 Regulatory Compliance: Achieved full compliance with PCI-DSS & ISO 27001
🧠 AI in Action
When a second breach attempt occurred a few weeks later:
The system flagged a login attempt from Russia using an Indian user’s credentials.
AI immediately compared this with the user’s behavioral pattern.
Automated triggers isolated the endpoint and revoked VPN access.
The entire chain of response — alert, contain, block, report — completed in less than 30 seconds.
💬 Client Testimonial
"We didn’t just upgrade our security — we changed our culture. The AI-driven SOC from Antarjal Suraksha is like having an intelligent bodyguard for our digital assets. It watches, learns, and acts faster than any human team ever could."
— CIO, National Retail Chain
Security
Innovative solutions for modern cybersecurity challenges.
Trust
Protect
info@vnss.cloud
+91 - 99803-18502
© 2025. All rights reserved.
Legal Policy
