SOC with AI: Revolutionizing Security Operations with Artificial Intelligence
"Transform Your Security Operations with AI-Driven SOC Solutions"
"Leverage the power of Artificial Intelligence to enhance your Security Operations Center, improving threat detection, response times, and operational efficiency like never before."
AI-Driven Security
Revolutionize your SOC with AI for enhanced threat detection and operational efficiency.


Real-Time Threat Detection: Traditional SOCs rely on predefined rule sets and human oversight to identify suspicious activities. AI, however, can learn from vast amounts of data to identify anomalies and patterns indicative of malicious behavior in real-time. This drastically improves detection capabilities, allowing you to spot threats faster and with greater accuracy.




Automated Incident Response: Speed is critical when responding to cyber threats. AI empowers your SOC with the ability to automate common security tasks, such as initial triage, alert prioritization, and even some response actions. With AI handling routine tasks, your security analysts can focus on high-priority incidents, improving overall response times and reducing the risk of human error.
Predictive Analytics for Threat Intelligence: By leveraging AI’s predictive capabilities, your SOC can analyze threat intelligence from a global pool of data sources to anticipate new attack trends. AI continuously monitors and analyzes evolving tactics, techniques, and procedures (TTPs) used by adversaries, ensuring that your SOC stays prepared for emerging threats.
AI-Enhanced SOC Features to Safeguard Your Business
Initial Assessment and Customization: Our team conducts a thorough assessment of your current security infrastructure and identifies areas where AI can make the most impact. We then design a customized AI-powered SOC solution that aligns with your organization’s unique needs and threat landscape.
AI Integration and Setup: Once the strategy is defined, we integrate AI technologies into your existing SOC infrastructure. This includes setting up machine learning models, AI-driven tools, and automation features tailored to your specific security objectives.
Continuous Monitoring and Optimization: Our AI-powered SOC operates 24/7, continuously monitoring your environment for threats. We also ensure that the system evolves and improves by leveraging ongoing machine learning and threat intelligence updates, adapting as cyber threats change over time.
Expert Support and Guidance: Even with AI at the core, human expertise is crucial. Our cybersecurity experts work alongside AI systems to refine detection algorithms, develop response strategies, and provide advanced threat mitigation when needed.




Case Study: Implementing AI-Powered SOC for a Leading Financial Services Firm
Client Profile:
A large financial services provider with 30+ branch offices across India, managing sensitive customer data and high-volume digital transactions.
Objectives:
Reduce incident response times.
Eliminate alert fatigue.
Ensure 24/7 threat detection with minimal manual intervention.
Improve regulatory compliance (ISO 27001, RBI Cybersecurity Guidelines).
Build resilience against advanced persistent threats (APT), phishing, and data exfiltration.
Phase 1: Initial Assessment and Customization
Process:
Conducted a 360-degree audit of the client's existing SOC setup.
Identified gaps in:
Threat intelligence correlation
Response orchestration
Real-time anomaly detection
Mapped current and historical incidents to determine high-risk vectors.
Worked with compliance and IT security teams to align SOC strategy with business objectives.
Outcome:
Customized a modular AI-SOC blueprint incorporating:
Machine Learning-based User & Entity Behavior Analytics (UEBA)
Automated playbooks for phishing and malware containment
Blockchain log integration for tamper-proof audit trails
Phase 2: AI Integration and Setup
Deployment Highlights:
Integrated AI/ML models for:
Behavioral threat modeling
Network anomaly detection
Predictive threat hunting
Setup included:
SOAR (Security Orchestration, Automation and Response) platform
Real-time dashboards and threat visualization
Blockchain-based log immutability (hyperledger-based setup)
Customization Elements:
AI models trained on over 5 million past events for context-aware responses.
Alert routing was adapted based on severity and department.
Phase 3: Continuous Monitoring and Optimization
24x7 Monitoring:
SOC monitored endpoints, cloud infrastructure, email gateways, and payment systems.
Real-time alerts integrated with Slack + email + native mobile app.
Implemented automated containment rules (e.g., isolate infected host, suspend user session).
Ongoing Optimization:
Weekly ML model tuning based on new threat intel feeds.
Monthly SOC performance audits.
Used client-specific attack simulations to enhance detection accuracy.
Phase 4: Expert Support and Guidance
Human-AI Collaboration:
Our Tier 3 analysts and threat hunters continuously:
Fine-tuned detection algorithms.
Provided deep-dive forensic analysis for critical incidents.
Trained client’s internal SOC team on AI toolkits.
Client Enablement:
Delivered custom training modules.
Built client-specific response runbooks for malware, insider threat, and third-party risk.
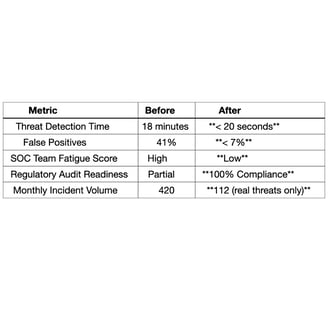
Results Achieved (Within 90 Days):

Client Testimonial:
“We went from being overwhelmed by noise to having clarity and control. The AI-Powered SOC has completely transformed our cyber resilience — backed by smart tech and smarter people.”
—
Conclusion:
By leveraging a structured approach combining AI, blockchain, and expert human support, we helped this client evolve from reactive security operations to a proactive, intelligent, and auditable SOC model.
Security
Innovative solutions for modern cybersecurity challenges.
Trust
Protect
info@vnss.cloud
+91 - 99803-18502
© 2025. All rights reserved.
Legal Policy
